VMware Horizon 7.0 GA - here’s what’s new (part 3 -True SSO and URL Content Redirection)
VMware Horizon 7.0 is now GA. Now we can finally take a look at all the new features in detail. This third part is about True SSO and URL Content Redirection.
True SSO
- For VMware Identity Manager integration, True SSO streamlines the end-to-end login experience. After users log in to VMware Identity Manager using a smart card or an RSA SecurID or RADIUS token, users are not required to also enter Active Directory credentials in order to use a remote desktop or application.
- Uses a short-lived Horizon virtual certificate to enable a password-free Windows login.
- Supports using either a native Horizon Client or HTML Access.
- System health status for True SSO appears in the View Administrator dashboard.
- Can be used in a single domain, in a single forest with multiple domains, and in a multiple-forest, multiple-domain setup.
Horizon 7 True SSO provides the ability to seamlessly sign onto a virtual desktop a single time using two-factor authentication via Identity Manager or Workspace ONE. True SSO separates authentication and access to Horizon-based desktops and applications.
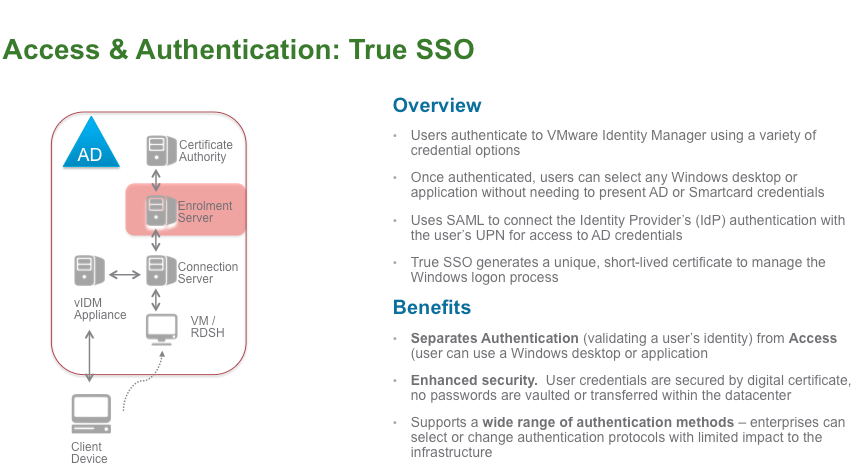 Previously, users could SSO into a virtual desktop seamlessly via Identity Manager when using active directory (AD) credentials. Now, True SSO supports a wide range of authentication methods, starting with two-factor authentication, such as RSA SecureID. True SSO requires configuration on Identity Manager, an additional enrollment server established in the Horizon 7 environment and a Microsoft Certificate Authority. True SSO can be enabled at the global or pool level with Horizon 7.
Previously, users could SSO into a virtual desktop seamlessly via Identity Manager when using active directory (AD) credentials. Now, True SSO supports a wide range of authentication methods, starting with two-factor authentication, such as RSA SecureID. True SSO requires configuration on Identity Manager, an additional enrollment server established in the Horizon 7 environment and a Microsoft Certificate Authority. True SSO can be enabled at the global or pool level with Horizon 7.
Benefits of True SSO
True SSO
- Separates authentication (validating a user’s identity) from access (such as to a specific Windows desktop or application).
- Provides enhanced security. User credentials are secured by a digital certificate. No passwords are vaulted or transferred within the data center.
- Supports a wide range of authentication methods. Selecting or changing authentication protocols has a limited impact on the infrastructure of the enterprise.
How True SSO Works
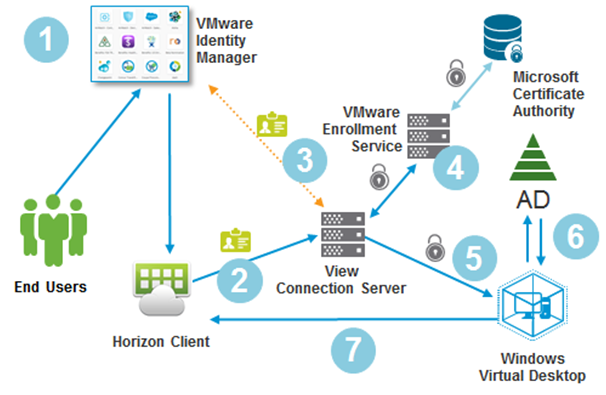
Figure 1: The True SSO Authentication Process
Figure 1 shows the flow of data in True SSO:
- A user authenticates to VMware Identify Manager. The administrator can select from an extensive set of authentication methods (RSA SecurID, RADIUS, Biometric, and so on). After authentication, the user selects a desktop or application to launch from VMware Identity Manager.
- Horizon Client is launched with the user’s identity, and credentials are directed to the View Connection Server, the broker for Horizon 7.
- The broker validates the user’s identify with Identify Manager by sending a SAML assertion.
- Using the certificate Enrollment Service, Horizon 7 requests that the Microsoft Certificate Authority (CA) generate a temporary, short-lived certificate on behalf of that user.
- Horizon 7 presents the certificate to the Windows operating system.
- Windows validates the authenticity of the certificate with Active Directory.
- The user is logged in to the Windows desktop or application, and a remote session is initiated on the Horizon Client.
True SSO does not rely on password vaulting, which risks compromising the credentials or having them become out of date, for example, with password changes. All authentication and access to enterprise assets are provided by digitally signed credentials and certificates.
Supported Authentication Methods for Identity Manager
Identity Manager supports the following authentication methods in conjunction with True SSO:
- RSA SecurID
- Kerberos
- RADIUS authentication
- RSA Adaptive Authentication
- Standards-based third-party identity providers
Identity Manager also supports integration with third-party identity providers to federate authentication across the enterprise.
Of course, Identity Manager also supports user name and password credentials as well as smart card logins, but for either of these, True SSO is not needed.
Infrastructure Requirements
True SSO requires a Horizon 7 environment, which includes the View Connection Server and Horizon Agent, as well as a new service called the Enrollment Service. The Enrollment Service can run on Windows Server 2008 R2 or Windows Server 2012 R2 (4 GB RAM is sufficient).
In addition, a Microsoft CA is required. The CA can run on Windows Server 2008 R2 or Windows Server 2012 R2.
For high availability (HA), VMware recommends a minimum of 2 certificate authorities and 2 Enrollment Servers. In an upcoming blog post in this series, we will discuss the various approaches to dealing with HA.
Desktop OS Support
True SSO is supported on all Windows guest operating systems that are supported for Horizon 7 desktops, from Windows 7 to Windows 10, along with Windows Server 2008 R2 and Windows Server 2012 R2. In addition, True SSO is supported on desktops and apps provided by Microsoft Remote Desktop Session Hosts running Windows Server 2008 R2 or Windows Server 2012 R2.
True SSO is supported with all display protocols, including Blast Extreme and HTML Access.
Access Point 2.5 Integration
- Smart card authentication is now fully supported.
- RSA SecurID and RADIUS authentication have been added.
- Smart policies can be used with Access Point.
- VMware Blast protocol can now be directed to port 443. Previously, port 8443 was required.
Note: Access Point 2.6 version serves as a reverse proxy for VMware Identity Manager only.
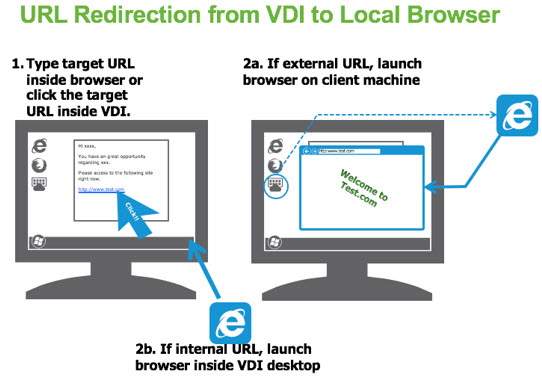
URL Content Redirection for Windows Horizon Clients
- For specific URLs, you can configure whether, when end users click a link to that URL in an Internet Explorer browser or an application, or if they type the URL into an Internet Explorer browser, that link gets opened always on a Windows-based client system or always in a remote desktop or application.
- URL links can be links to Web pages, telephone numbers, email addresses, and more.
- Configured through group policy.
Allows to redirect URL from VDI to the local browser. Admin can configure policies to control whether user can access the content with application on the server or the client. Supports HTTP and HTTPs. Some possible use cases:
- Work around browser incompatibility issues ( for example IE 10 in VDI desktop and IE 7 on client device)
- Separate internal browsing from external browsing domains.
- Allows to secure the environment because content which is potentially dangerous is executed on the client computer instead on the VDI desktop
- Offload resource intensive web operations to the local client.
You can configure GPO which does restrict the content that will be opened in a browser inside VDI over Browser on the client’s PC.